techcarrot Information Security Management System (ISMS)
Information Security
- What is Information Security?
Information Security is the protection of internet-connected systems such as hardware, software and data from cyberthreats. The practice is used by individuals and enterprises to protect against unauthorized access to data centres and other computerized systems.
- How it affects your privacy?
Cyberattacks are now the fastest growing crime on a global scale. Financial losses from cyber crime exceed the total losses incurred from the global trade of all illicit trading. Aside from financial losses, such forms of cyber-attacks can lead to reputation damage as well. Consumer & user data, when compromised, can subject businesses to strict regulations and costly settlements. Security deficiencies are costing for profit and non-profit organizations billions of dollars in losses. Plus, with companies shifting to remote work since the pandemic began, they have become more vulnerable to attacks from hackers.
Information Security Trends for 2022/2023
Cyberattacks are now the fastest growing crime on a global scale. Financial losses from cyber crime exceed the total losses incurred from the global trade of all illicit trading. Aside from financial losses, such forms of cyber-attacks can lead to reputation damage as well. Consumer data, when compromised, can subject businesses to strict regulations and costly settlements.
Security deficiencies are costing for profit and non-profit organizations billions of dollars in losses. Plus, with companies shifting to remote work since the pandemic began, they have become more vulnerable to attacks from hackers.
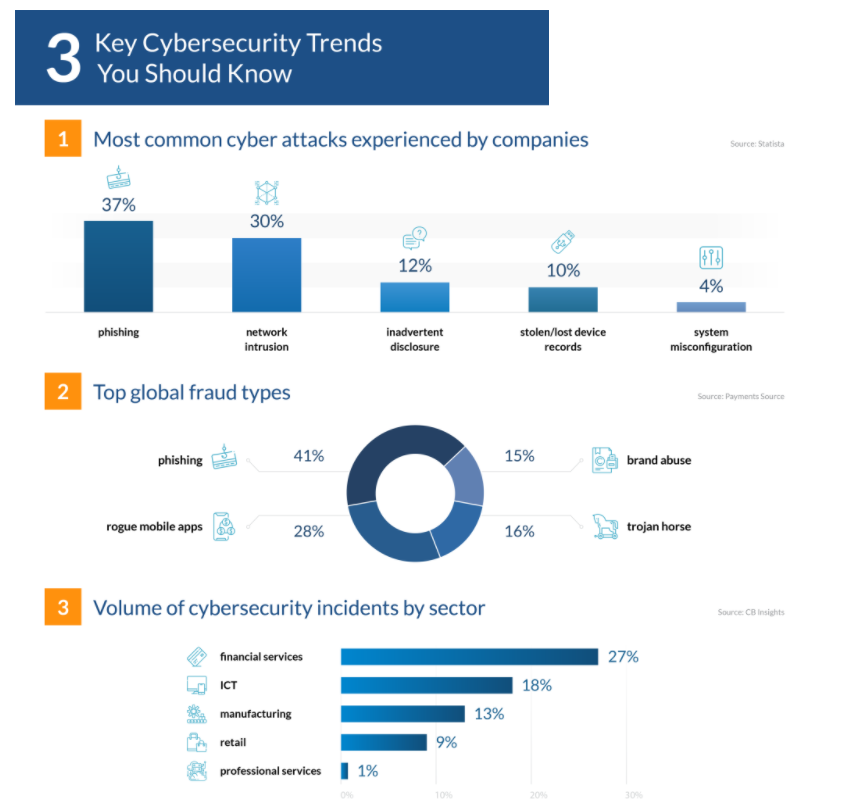
Few Astonishing Facts-
- About 97% of the people in the world cannot identify a phishing email.
- About 32% of data breaches globally involved phishing activities.
- Predictive security cloud gained a 261% ROI in the last three years.
- About 50% of businesses believe they were already GDPR-compliant by the end of 2018.
- Out of 17 industries in the US, the higher education sector comes in last when it comes to cybersecurity.
- Infected routers account for 75% of all IoT attacks that occurred in 2018.
- About 70% of fraudulent transactions occurred through mobile channels.
- Attacks on financial institutions spiked by a massive 238% during COVID-19.
- Attacks now cost the banking industry $18.3 million per enterprise.
- Mobile devices are popular attack vectors for cyber criminals.
What is Information Security Management System (ISMS)?
An information security management system (ISMS) is a set of policies and procedures for systematically managing an organization’s sensitive data. The goal of an ISMS is to minimize risk and ensure business continuity by pro-actively limiting the impact of a security breach.
An ISMS typically addresses employee behavior and processes as well as data and technology. It can be targeted towards a particular type of data, such as customer data, or it can be implemented in a comprehensive way that becomes part of the company’s culture.
ISO 27001 is a specification for creating an ISMS. It does not mandate specific actions, but includes suggestions for documentation, internal audits, continual improvement, and corrective and preventive action.
How is ISMS helping techcarrot?
1. Secure information in all its forms: An ISMS helps protect all forms of information, whether digital, paper-based or in the Cloud.
2. Increase attack resilience: Maintaining an ISMS will significantly increase organization’s resilience to cyber-attacks.
3. Manage all your information in one place: An ISMS provides a central framework for keeping your organization’s information safe and managing it all in one place.
4. Respond to evolving security threats: Constantly adapting to changes both in the environment and inside the organization, an ISMS reduces the threat of continually evolving risks.
5. Reduce costs associated with information security: Thanks to the ISMS’s risk assessment and analysis approach, organizations can reduce costs spent on indiscriminately adding layers of defensive technology that might not work.
6. Protect the confidentiality, availability and integrity of organization’s data: An ISMS offers a set of policies, procedures, technical and physical controls to protect the confidentiality, availability and integrity of your information.
7. Improve company culture: An ISMS’s holistic approach covers the whole organization, not just IT. This enables employees to readily understand risks and embrace security controls as part of their everyday working practices.
Why is ISMS important?
- Protects information from a range of threats
- Ensures business continuity
- Minimizes financial loss
- Optimizes return on investments
- Increases business opportunities
- Need to preserve CIA-
- (C) Confidentiality– Ensuring that information is accessible only to those authorized to have access
- (I) Integrity– Safeguarding the accuracy and completeness of information and processing methods
- (A) Availability– Ensuring that authorized users have access to information and associated assets when required
Organization Survival depends on Information Security. Security breaches leads to-
- Reputation loss
- Financial loss
- Intellectual property loss
- Legislative Breaches leading to legal actions (Cyber Law)
- Loss of customer confidence
- Business interruption costs
- Loss of Goodwill
Risk, Threats, Vulnerabilities & Controls
Risk: A possibility that a threat exploits a vulnerability in an asset and causes damage or loss to the asset.
Threat: Something that can potentially cause damage to the organization, IT Systems or network.
Vulnerability: A weakness in the organization, IT Systems, or network that can be exploited by a threat.
Controls: A practice, procedure or mechanism that reduces risk
Most Common Threat to an IT Ecosystem
- Malwares & Other Computer Viruses
- Tailgating
Malware: Malware is an umbrella term for any piece of software that has malicious intent. There are several types of malwares and each of them has a unique way of infiltrating your computer which may include attempts at gaining unauthorized control of your computer systems, stealing your personal information, encrypting your important files, or causing other harm to your computers. Sometimes the damage can be irrevocable.
Where does malware come from?
Some of the most common sources of malware are email attachments, malicious websites, torrents, and shared networks.
- Phishing – Emails can be disguised to be coming from a fraudulent company for the sole purpose of getting you to reveal personal information
- Malicious Websites – Some websites may attempt to install malware onto your computer, usually through popups or malicious links
- Torrents – Files shared through BitTorrent are generally unsafe because you never know what to expect until they’re downloaded
- Shared Networks – A malware-infected computer on the same shared network may spread malware onto your computer
Tailgating
Tailgating attack is said to be a social engineering effort by the cyber threat actors who trick staff of an organization into assisting them in gaining illegal or unwarranted access into the company’s work environment.
Examples-
- A social engineer can fake to be a supply agent from an e-commerce firm or somebody from a food vendor with some boxes on their hands as an excuse to ask workers to open the door. The social engineer would fake to make it look uneasy for him to open the door and would ask any approved individual to assist him as a courtesy to get right of entry to the restricted premises.
- Tailgaters enter an unauthorized place is by hanging around places where people engage in tea breaks and smoking. The Social engineer would appear like every other staff, thereby engaging in a discussion with any of the workers. At the end of the break, the social engineer will still engage the worker in a dialog and consequently follow him/her to enter the building as the staff opens the door unsuspecting.
Developments in the Information Security Arena
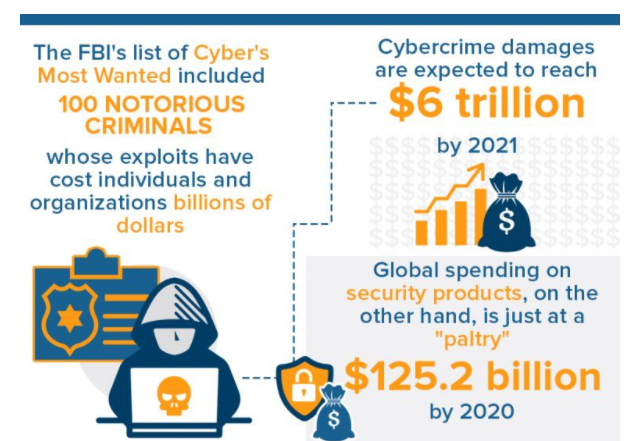
As cyber threats become more aggressive each day, businesses and organizations take major steps to strengthen their security measures. For many establishments, cybersecurity awareness is essential to prevent costly identity theft and network hacks that can destroy any company or individual’s reputation. Apart from implementing firewalls and sophisticated IT protocols, companies now deem it important to augment the capabilities of their IT personnel via seminars and trainings. After all, 80% of data breaches can easily be prevented by practicing cyber hygiene.

By comparison, global spending on security products was just at a “paltry” $125.2 billion in 2020. How would that deal with the ever-growing sophistication of cyber criminals out there is an open question. The lucrative cyber crime underground is proving to be a tough hydra to deal with, generating spawns in large numbers—and types.
Top 10 Quick & Effective Information Security Tips for techcarrot’s employees
1. Users are not allowed to disable the anti-virus software residing on their desktop and/or laptops. The Corporate Anti-Virus program must be updated on their Desktop and/or Laptop.
2. User passwords should remain confidential and not shared, posted, or otherwise revealed in any manner.
3. Users are prohibited from using any automated tools or any other means for gaining unauthorized entry into any third-party systems or any resource over the Internet to which they do not have authorized access rights.
4. No user is permitted to send sensitive and confidential data through the organization’s email without the use of encryption software.
5. Organization shall follow a Four scale grade for classifying its asset-
- Strictly Confidential
- Confidential
- Internal Use Only
- Public
6. Users must not leave their laptops unattended even for few minutes for example, in public area, airports, etc.
7. Users must lock their account when leaving the Desktop and/or Laptop unattended. They are prohibited to connect their personal Laptops, cameras, or combined devices to the organization’s network.
8. Always clear your workspace before leaving for longer periods of time. Use the recycling bins for sensitive documents when they are no longer needed. Consider scanning paper items and filing them electronically in your workstation.
9. Every access to the offices from outsiders, e.g., visitors, or other departments must be recorded at the main door.
10. Always be careful & review phishing emails with the following characteristics before responding to such emails-
- Insisting on Urgent Action
- Containing Spelling Mistakes & with an Unfamiliar Greeting
- Inconsistencies in Email Addresses, Links and Domain Names
- Be Wary of Suspicious Attachments
- That Seem Too Good to Be True
- Requesting Login Credentials, Payment Information or Other Sensitive Information
References:
1. Eagle Edge,
2. TechTarget,
3. FinancesOnline,
4. CyberSecurityVentures
5. TitanFile
6. FinancesOnline
View All Blogs






